Teams Gateway Settings
Device Policy
The RealConnect Service for Microsoft Teams allows administrators to define a standards-based video teleconferencing system (VTC) which is using the service to join a Microsoft Teams meeting as either a Trusted or Untrusted device. This capability allows administrators to allow some VTCs to bypass the meeting lobby while other VTCs are placed into the lobby.
This feature is not applicable when connecting through the service to Skype meetings as Cloud Video Interop (CVI) does not support lobby bypass with Skype for Business.
Summary
The available configuration in the service allows for either allow-list or block-list behavior to be defined by using specific IP addresses and/or subnets to control which devices are defined as trusted or as untrusted. How a calling device is defined by the service will impact whether Microsoft Teams places that participant in a meeting’s lobby or not. In most cases a trusted device will bypass the attendee lobby while an untrusted device will be placed into the lobby, but the behavior depends on the configuration of the specific Microsoft Teams meeting that is being joined.
Trusted Devices
A trusted device will directly join a meeting when the scheduled meeting is configured to allow participants from the organizer's own organization to bypass the lobby. This means that a trusted device will bypass the lobby for every possible Teams meeting configuration other than meetings in which only the organizer is allowed to bypass the lobby (see the following note). Only trusted devices can join a Microsoft Teams Live Event and will join the event as a potential presenter (if selected by the event producer).
Note: By design, a trusted device currently bypasses the lobby in a Microsoft Teams meeting regardless of the lobby settings for the meeting. Microsoft is investigating options to change the lobby bypass action of trusted devices.
Untrusted Devices
An untrusted device will be placed into the meeting lobby of a Microsoft Teams meeting, thus will need to be manually admitted by a native trusted participant. Note: Untrusted devices cannot attend or participate in a Microsoft Teams Live Event.
One exception to this behavior is when a Microsoft Teams meeting is configured to allow "Everyone" to bypass the lobby. For these meetings, any VTC joining via the RealConnect Service will directly join the meeting as both trusted and untrusted participants are automatically admitted through the lobby by Microsoft Teams. Untrusted devices cannot start a Teams meeting by default, so any untrusted VTCs joining one of these meetings before the first trusted participant joins will temporarily be staged in the lobby. Once a trusted participant joins the meeting then all attendees in the lobby will automatically be admitted into the meeting.
Enable Lobby Bypass
The ability to enable a tenant-wide lobby bypass feature has been available since the RealConnect Service for Microsoft Teams was launched and this parameter may have already been customized during or after the initial configuration of the service for a given Microsoft Office 365 tenant.
Either way, for the RealConnect Service to be allowed to define any devices as trusted then the Lobby Bypass feature for CVI must first be enabled on the Microsoft 365 tenant. This is performed via PowerShell by setting the AllowAppGuestJoinsAsAuthenticated parameter to '$true' as outlined here.
Note: Changes to this parameter can take several hours to apply to the Microsoft tenant. Enabling this setting simply means that Teams will now allow the RealConnect Service to define a connection as trusted instead of treating all connections as untrusted.
If this parameter remains set to the default value of '$false' then all VTCs will still automatically bypass the lobby for meetings set to automatically admit Everyone from the lobby. Also be aware that none of the additional Trusted Device configuration options covered on this page will function.
Service Configuration
Once Lobby Bypass has been enabled on the tenant then individual devices or entire networks can be defined as trusted (or untrusted) by using the Trusted Device Configuration link provided on the Poly RealConnect administration portal. To access this portal a user account assigned the Global Admin role in the Microsoft 365 tenant is required. This configuration page provides two layers of control:
- An on/off setting to control all calls from unknown devices as either trusted or untrusted.
- A customizable policy to define known devices and if they are individually treated as trusted or untrusted.
Changes to either of these settings are immediate and will be applied to any new calls into the service.
Unknown Devices
The first option is the setting Trust incoming calls from unknown devices and is applied to any device which does not match any specific rule defined in the policy list. This setting is already enabled by default for all new and existing RealConnect customers.
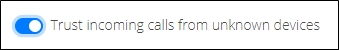
Once the prerequisite Lobby Bypass feature is enabled via PowerShell then because the above service setting is enabled by default then all calls into the RealConnect Service from any VTC to meetings scheduled by users in this tenant will be treated as trusted devices. Disabling this setting will tell the service to treat all devices as untrusted, returning the tenant to original behavior of calls going into the lobby in most scenarios. This setting's behavior is not applicable to any known devices which are later defined via the configuration in the following section.
Known Devices
The second option allows for the creation of multiple policies which can be used to define calls coming from specific source IP addresses or subnet ranges. Devices matching any enabled rules defined here will be identified as known and in turn will be individually treated as either trusted or untrusted, depending on the configuration in specific policy entry.
When no policies exist then all calls into the RealConnect Service are treated as coming from unknown devices and will be handled based on the configuration of Lobby Bypass and Unknown devices settings outlined above.
Adding a device policy allows any devices which match the provided IP address or range to be treated as trusted or untrusted, depending on that policy's configuration.
Currently there are four configuration settings provided in the device policy:
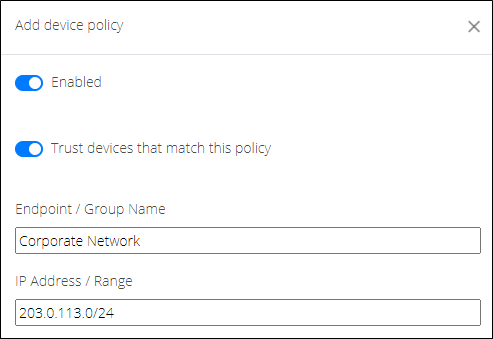
- Enabled - Tells the RealConnect Service whether to use or ignore this device policy. This setting would be used to temporarily disable a rule without deleting it.
- Trust devices that match this policy - Any device matching this policy will be treated as trusted when enabled or as untrusted when disabled. Using this setting in conjunction with the global setting applicable to all unknown devices is essentially how an allow-list (or block-list) behavior would typically be configured for the service.
- Endpoint / Group Name - Any descriptive name used to identify the individual rule to the administrator. This field must be unique among any other policy names.
- IP Address / Range - The IP address or subnetwork range used to match incoming calls to this device policy.
The IP Address / Range field can include any of the following supported notations:
| Individual | 203.0.113.77 |
| Range | 203.0.113.0 - 203.0.113.255 |
| Shortcut Range | 203.0.113.0 - 255 |
| Classless Inter-Domain Routing (CIDR) | 203.0.113.0/24 |
| Netmask | 203.0.113./255.255.255.0 |
Whether using SIP and/or H.323 protocols to place calls into the service both internal local and external public IP addresses can be used to identify devices, depending on the registration status of the calling endpoints. The public IP address typically is applied to the endpoint's call by the last Network Address Traversal (NAT) device it passed through before reaching the public Internet. This could be a standards-based video traversal system (like a Polycom RPAD or Cisco VCS-E) or any standard IP firewall solution.
- Registered Endpoints are registered to a SIP and/or H.323 registrar and calls placed from the endpoint will not appear to originate from the device itself but instead will appear to the service as coming from the registrar's external identity. These calls can only be identified by the public IP address associated with the registrar.
- Unregistered Endpoints are not registered to a H.323 or SIP registrar when placing calls into the RealConnect Service. These calls can be identified by using either their local private IP address or their public IP address.
When attempting to select the correct IP address(es) needed for a specific endpoint it can be helpful to reference the Calls List section of the RealConnect Tenant Reports. The sourceIP field listed in the Call Details for a successful call into the service by the desired endpoint will contain the IP address which needs to be included in the device policy.
Icon Legend
| Icon | Description |
|---|---|
| Trusted Device/Network | |
| Untrusted Device/Network | |
| Disabled policy | |
| Add new device policy | |
| Edit selected policy | |
| Delete selected policy |
Custom IVR Prompts
RealConnect provides the option to customize the IVR (Interactive Voice Response) prompts in the service.
The following IVRs can be customized to your needs:
- Welcome
- Conference ID
- Lobby
- Waiting for participants
Set a Custom IVR Prompt
- Go to the RealConnect Service (webapp.plcm.vc).
- Log in to RealConnect (requires a Microsoft Office 365 Global admin account).
- Select Teams Gateway Settings, from the Teams Configuration section.
- Select the Custom IVR Prompts tab.
- Select Using Custom Prompts, this will display the graphic and voice file requirements.
- To upload a file, select the Upload icon on the upper right corner of the graphic.
- Select the file to upload and select Open.
- If the image meets the requirements, it will display.
Note: A Powered by Poly banner will be displayed on the bottom of your graphic. - To add a custom IVR audio file, select the Upload icon on the right of the audio section.
- Select the audio file to upload and select Open. Test the sound file.
- When both graphic and video files meet your requirements, select the arrow on the graphic to move to the next IVR to modify.
Note: If you do not want the updated file, select the Revert icon (next to the upload icon). - Repeat the process for each of the IVRs.
- When complete, select Save.
- Select Exit.
File Requirements
Slide Requirements
- Dimensions: 1920 x 1080
- Accepted formats: bmp, gif, jpg, and png
- No alpha channels
Audio Requirements
- 16-bit PCM
- Monophonic Audio
- 16kHz
- WAV file format
Miscellaneous
Enable MCU Detection - A forced-speaker-switch layout will be sent to Poly MCUs when this setting is enabled, otherwise the default VTC layout will be used.
Use Video-Prioritized Layout - A video-prioritized layout only displays video-enabled participants. If no video-enabled participants exist, then the video-muted participants will be displayed.